Change Pointers How To In Ecc
Create a new Replication Model entry Assign Outbound Implementation 986_3 Outbound Impl. Motor car attested from 1895 is the usual formal term in British.

Sap Global Track And Trace Part 2
The external interface to the module cannot change in any way that would break another module or markup language either within or outside of the W3C.

. On STE based on change pointers. 2 Also notice there are two files not in the ecc folder I deleted independent of this change. Ebook ou e-book aussi connu sous les noms de livre électronique et de livrel est un livre édité et diffusé en version numérique disponible sous la forme de fichiers qui peuvent être téléchargés et stockés pour être lus sur un écran 1 2 ordinateur personnel téléphone portable liseuse tablette tactile sur une plage braille un.
A method for managing a readahead cache in a memory subsystem based on one or more active streams of read commands is described. The proc file system acts as an interface to internal data structures in the kernel. So would be to manually change a pointer as the obfuscation key used for the pointer would be very hard to retrieve.
Local variable DATA. 32 pages of 51216 bytes each for a. 15 Using R interactively.
When you use the R program it issues a prompt when it expects input commands. So fast in fact that they are idle most of the time as they are waiting for memory to arrive from global memory. I have adopted reverse engineering process rather than understanding.
In Chapter 2 we show you how you can use procsys to change settings. This will help to understand the SD concepts as well. Change the frame-related functions in the inspect module to return a regular object that is backwards compatible with the old tuple-like interface.
ASCII characters only characters found on a standard US keyboard. The time taken to erase blocks can be significant thus it is beneficial to erase unused blocks. While a block device layer can emulate a disk drive so that a general-purpose file system can be used on a flash-based storage device this is suboptimal for several reasons.
A 3D data visualisation map from Cervest shows large swathes of Dublin could be affected by climate change-related coastal flooding in the years to come which could have big implications for the regions datacentres. The method used to read NAND flash memory can cause nearby cells in the same memory block to change over time become programmed. The output energy is usually measured in terms of absolute irradiance and the wall-plug efficiency is given as a percentage.
Instead of confusing those file deletions with ecc Ill make a different cleanup branch later to reflect those files deletion. A kernel is defined using the __global__ declaration specifier and the number of CUDA threads that execute that kernel for a given. You can also mix these resilient structures with the redundancyECC scheme for additional security or encode your most important data structures as resilient and the rest the expendable data that you can recompute from the main data structures as normal data structures with a bit of ECC or a parity check which is very fast to compute.
A footnote in Microsofts submission to the UKs Competition and Markets Authority CMA has let slip the reason behind Call of Dutys absence from the Xbox Game Pass library. 6 to 30 characters long. If Yes What is recommended approach for master data distribution material customers etc.
For the new Assignment line as next step create a new assignment line and enter the target business system for the replication model. A kernel is defined using the __global__ declaration specifier and the number of CUDA threads that execute that kernel for a given. Le livre numérique en anglais.
It originally referred to any wheeled horse-drawn vehicle such as a cart carriage or wagon. The method includes receiving a read command that requests data from a memory component and determining whether the read command is part of an active stream of read commands based on a comparison of a set of addresses of the read. Typical block sizes include.
CUDA C extends C by allowing the programmer to define C functions called kernels that when called are executed N times in parallel by N different CUDA threads as opposed to only once like regular C functions. The English word car is believed to originate from Latin carrus carrum wheeled vehicle or via Old North French Middle English carre two-wheeled cart both of which in turn derive from Gaulish karros chariot. Each entry in the array represents an element a ij of the matrix and is accessed by the two indices i and jConventionally i is the row index numbered from top to bottom and j is the column index numbered from left to right.
From the previous section we have seen that Tensor Cores are very fast. The content model cannot change in any way that would cause a previously valid document to become invalid. Must contain at least 4 different symbols.
1 In the output you can see the changes from the ECC packages upgrade including the addition of new files. Storing a sparse matrix. Use grep -E instead of egrep setopt.
Thus it is made hard for any unauthorized user of the function pointer to be able to actually use it. Flash memory blocks have to be explicitly erased before they can be written to. Lt_extension2 TYPE STANDARD TABLE OF bapiparex.
The default prompt is which on UNIX might be the same as the shell prompt and so it may appear that nothing is happeningHowever as we shall see it is easy to change to a different R prompt if you wish. Purpose of this document is mentioned below. Right click and copy the link to share this comment.
For a transformation from SAP ECC 60 in Cloud to SAP S4 HANA what deployment model would be most suitable and feasible. For an m n matrix the amount of memory required to store the. Not to understand SD concept but to understand what is exactly required to understand by Finance team from SD Module.
Check the ABAP source code below that we developed to dynamicly interpret the EXTENSION2 and change the structures. CUDA C extends C by allowing the programmer to define C functions called kernels that when called are executed N times in parallel by N different CUDA threads as opposed to only once like regular C functions. Wasm targets require function pointers to be called with the correct signatures so this led to crashes.
Use the handler table for protocol name to number conversions. In optical systems such as lighting and lasers the energy conversion efficiency is often referred to as wall-plug efficiencyThe wall-plug efficiency is the measure of output radiative-energy in watts joules per second per total input electrical energy in watts. The problem is now fixed.
For BPREL via Services Communication Channel Replication via Services and Filter time Filter After Change Analysis. If either of the above constraints would be violated by a change the working group will. Dublin datacentre operators warned of climate change-related coastal flooding risks.
Store is to be updated the file system will write a new copy of the changed data to a fresh block remap the file pointers. Dont reset recvsend function pointers on renegotiation. Ban server ALPN change during recv renegotiation.
Function pointers are obfuscated by XOR-ing with a random number so that the actual address pointed to is hard to retrieve. It can be used to obtain information about the system and to change certain kernel parameters at runtime sysctl. Lets see how the BAdI source code is being designed to interpret that and change the tables.
When POST is set reset the upload field. A matrix is typically stored as a two-dimensional array. When importing PFX disable key persistence.
First well take a look at the read-only parts of proc.

Scheduling Sap Background Job With Dynamic Date Parameter

Best Practices For Sap Jitterbit Success Central Jitterbit Success Central
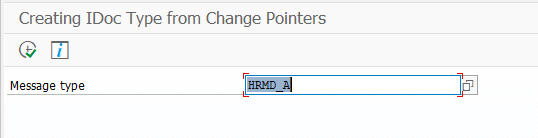
Sap Change Pointers In 4 Steps
设备主数据ale同步配置 Lvzhqi的博客 Csdn博客
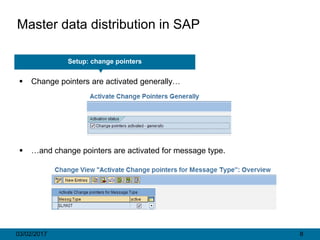
Master Data Distribution In Sap Implementation Guide
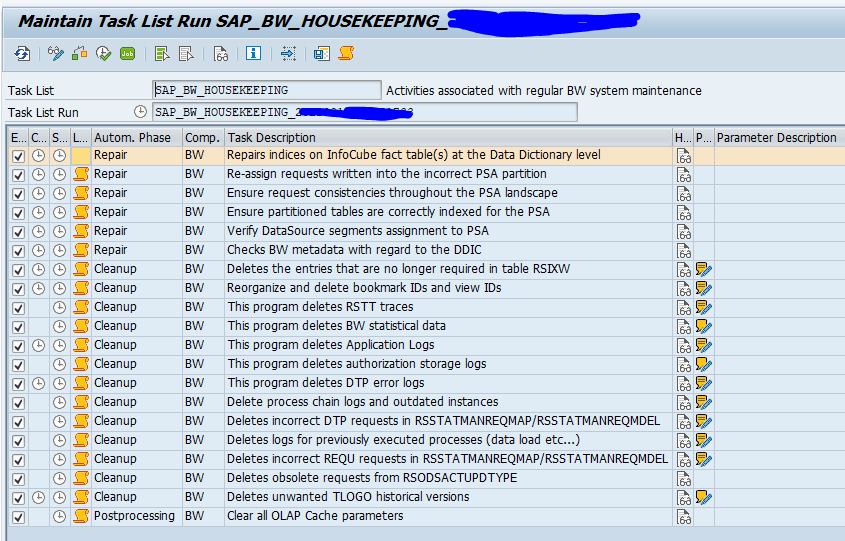
Data Volume Saptechnicalguru Com
Change Pointers In Sap Abap Sapignite

Sending Idoc S Automatically Using Change Pointers Sap Blogs

Confluence Mobile Support Wiki

Activating Change Pointers In Sap Ecc For Sap Gts Sapboost Com

10 Answer Change Pointers How To In Ecc Most Accurate Legoland

Activating Change Pointers In Sap Ecc For Sap Gts Sapboost Com

Enable Delta On Enhanced Custom Field In Change Pointer Based Datasource Multiple Target Systems Sap Blogs

Activating Change Pointers In Sap Ecc For Sap Gts Sapboost Com

Outbound Idoc By Change Pointers And Customized Triggering Events Sap Blogs
Github Applexuslabs Aws Sap Idoc Tricks Integrating Sap S Idoc Interface Directly Into Aws Api Gateway And Aws Lambda
Change Pointers In Sap Abap Sapignite